Obtaining a Long-Term Valid Login Command¶
Scenario¶
This section describes how to obtain a login command that is valid for a year.
Note
For security purposes, it is advised to obtain the login command in the development environment.
Process¶
You can obtain a long-term valid login command as the following process:

Figure 1 Process¶
Procedure¶
Obtain the programmatic access permission. (If the current user has the permission, skip this step.)
Log in to the management console as an administrator.
Click
 in the upper left corner and select a region and a project.
in the upper left corner and select a region and a project.Click
 in the navigation pane on the left and choose Management & Governance > Identity and Access Management.
in the navigation pane on the left and choose Management & Governance > Identity and Access Management.Enter the name of the user to whom you want to grant the programmatic access permission in the search box on the Users page.
Click the user to go to its details page.
Click
 next to Access Type.
next to Access Type.Select Programmatic access. (You can select only programmatic access or both access types.)
Obtain the region, project name, and image repository address.
Log in to the management console, click your username in the upper right corner, and click My Credentials.
On the Projects tab page, search for the project corresponding to the current region.
Obtain the image repository address by referring to 1.b. The domain name at the end of the login command is the image repository address.
Obtain an AK/SK.
Note
The access key ID (AK) and secret access key (SK) are a pair of access keys used together to authenticate users who wish to make API requests. The AK/AS pair provides functions similar to a password. If you already have an AK/SK, skip this step.
Log in to the management console, click your username in the upper right corner, and click My Credentials.
On the Access Keys tab page, click Add Access Key.
Enter the login password and verification code sent to your mailbox or mobile phone.
Download the access key, which includes the AK and SK.
Note
Keep the access key secure and do not disclose it to any unauthorized personnel.
Log in to a Linux PC and run the following command to obtain the login key:
printf "$AK" | openssl dgst -binary -sha256 -hmac "$SK" | od -An -vtx1 | sed 's/[ \n]//g' | sed 'N;s/\n//'
In the command, $AK and $SK indicate the AK and SK obtained in Step 3 respectively.
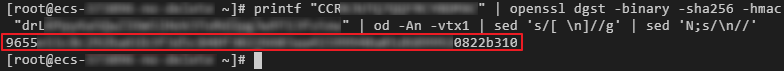
Figure 2 Sample command output¶
Put the information you obtained in the following format to generate a long-term valid login command:
docker login -u [Regional project name]@[AK] -p [Login key] [Image repository address]
In the command, the regional project name and image repository address are obtained in Step 2, the AK in Step 3, and the login key in Step 4.
Note
The login key is encrypted and cannot be decrypted. Therefore, other users cannot obtain the SK from -p.
The login command can be used on other devices.
Run the history -c command to clear the operation records.