SAML-based Federated Identity Authentication¶
This section describes the process and configuration of SAML-based federated identity authentication between an enterprise identity provider and the cloud system.
Caution
To implement federated identity authentication, ensure that your identity provider server and the cloud system use the same Universal Time Coordinated (UTC) time.
Ensure that your identity provider system supports SAML 2.0.
Configuring Federated Identity Authentication¶
To implement federated identity authentication between an identity provider and the cloud system, complete the following configuration:
Establish a trust relationship and create an identity provider: Exchange the metadata files of the identity provider and cloud system (see Figure 1).
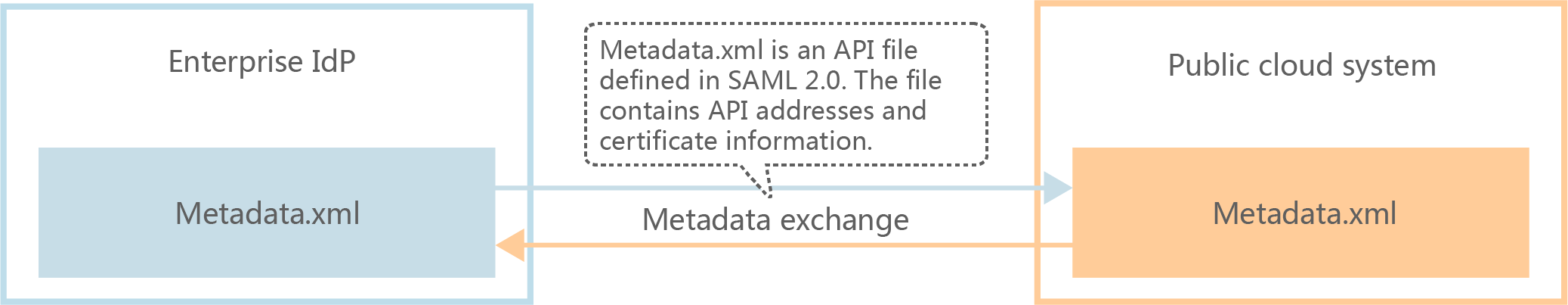
Figure 1 Metadata file exchange model¶
Configure identity conversion rules: Map the users, user groups, and permissions of the identity provider to the cloud system (see Figure 2).
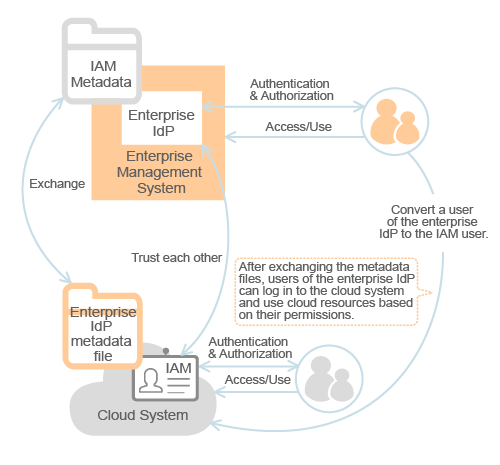
Figure 2 User identity conversion model¶
Configure a login link: Configure a login link (see Figure 3) in the enterprise management system to allow users to access the cloud system through SSO.
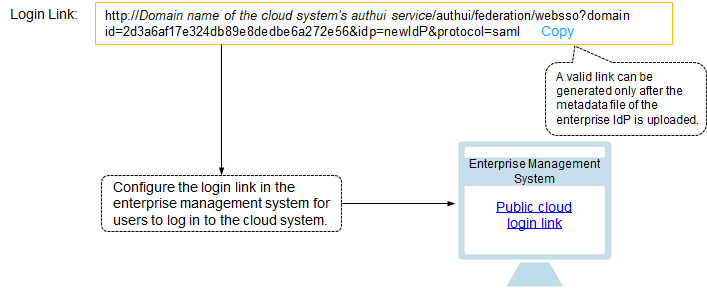
Figure 3 SSO login model¶
Process of Federated Identity Authentication¶
Figure 4 shows the interaction between an identity provider and the cloud system after a user initiates an SSO request.
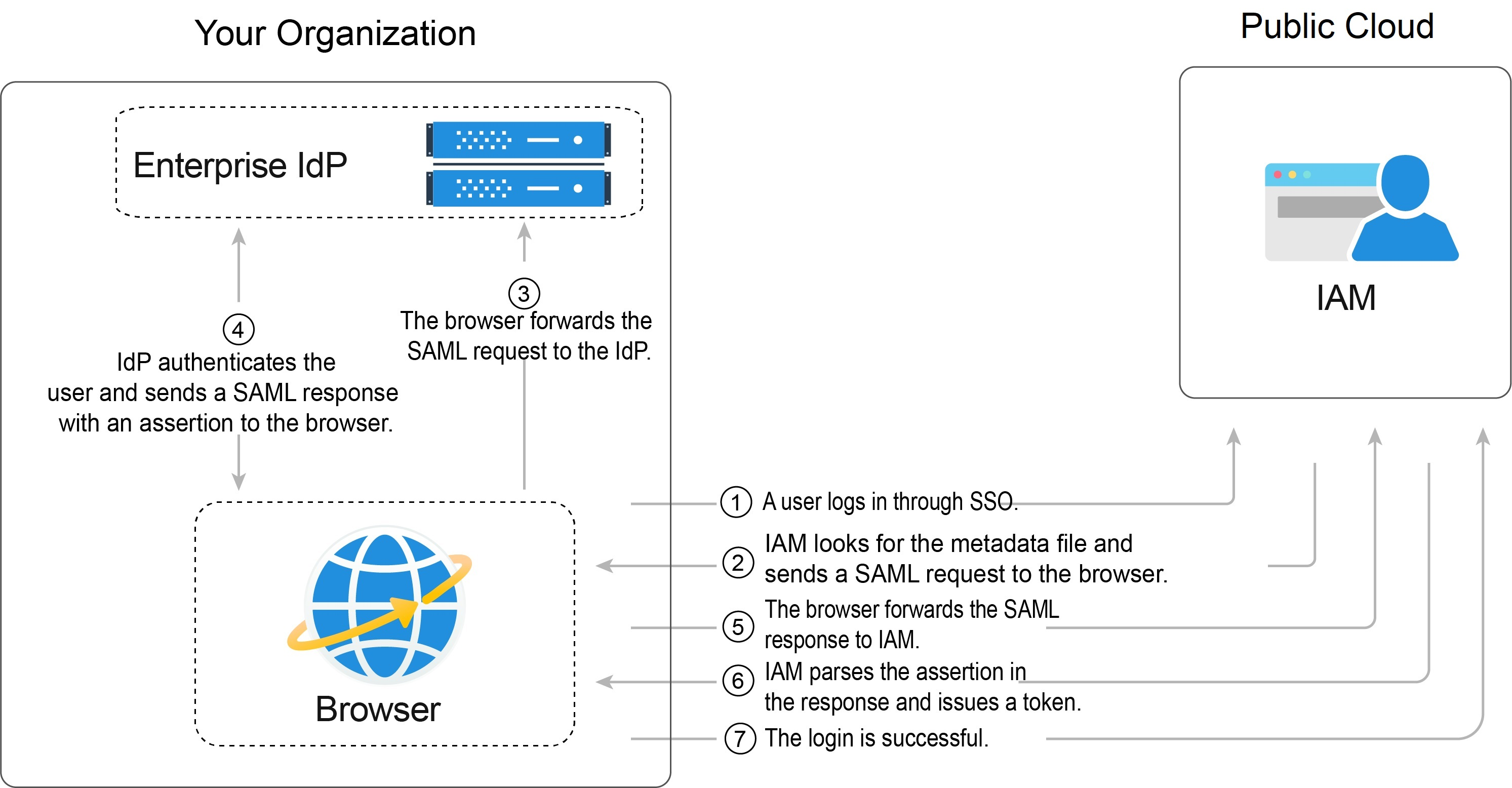
Figure 4 Process of federated identity authentication¶
Note
To view interactive requests and assertions with a better experience, you are advised to use the Google Chrome browser and install the SAML Message Decoder plug-in.
As shown in Figure 4, the process of federated identity authentication is as follows:
A user uses a browser to open the login link obtained from IAM, and then the browser sends an SSO request to the cloud system.
The cloud system searches for a metadata file based on the login link, and sends a SAML request to the browser.
The browser forwards the SAML request to the enterprise identity provider.
The user enters their username and password displayed in the identity provider system. After the identity provider authenticates the user's identity, it constructs a SAML assertion containing the user information, and sends the assertion to the browser as a SAML response.
The browser responds and forwards the SAML response to the cloud system.
The cloud system parses the assertion in the SAML response, and issues a token to the user after identifying the group to which the user is mapped, according to the configured identity conversion rules.
If the login is successful, the user accesses the cloud system successfully.
Note
The assertion must carry a signature; otherwise, the login will fail.