Permissions¶
Permission Description¶
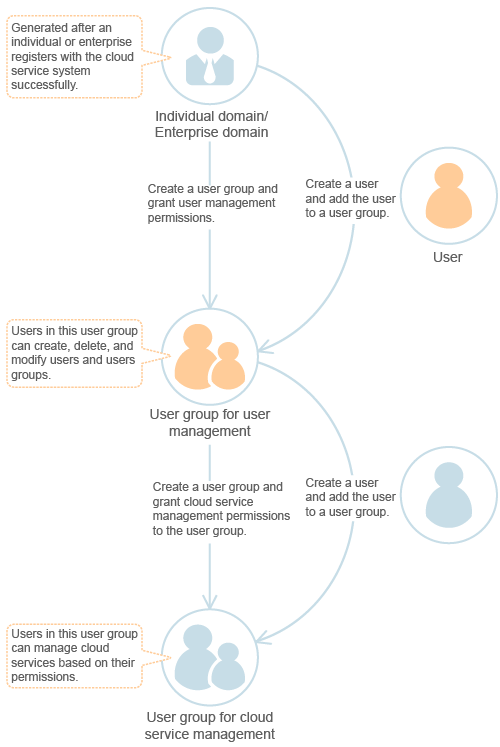
Permissions are user management and cloud service management permissions. User management involves creating, deleting, and modifying users and granting permissions to users. Cloud service management involves creating, viewing, modifying, and deleting resources of cloud services. After granting user management and cloud service management permissions to a user group, the users added to the user group can inherit permissions of the user group. User group-specific permissions simplify permission management.
Permission Relationship¶
Default Permissions¶
The system provides two types of default permissions: user management and cloud service management.
Node Name | Permission Name | Description |
|---|---|---|
Base | Security Administrator | Users with this permission can:
|
IAM | Agent Operator | Users with this permission can switch to an entrusted user for processing services. |
Currently, policies only support fine-grained authorizationof ECS, EVS, and VPC. ECS Admin, ECS User, ECS Viewer, EVS Admin, EVS Viewer,VPC Admin, and VPC Viewer are preset fine-grained authorization policies.
Permission Name | Managed Cloud Resource | Description |
|---|---|---|
Agent Operator | Identity and Access Management | Permissions for switching roles to access resources of delegating accounts. |
AutoScaling Administrator | Auto Scaling | Full permissions for all AS resources. This role must be used together with the Tenant Guest, Server Administrator, ELB Administrator and CES Administrator roles in the same project. |
AutoScaling FullAccess | Auto Scaling | All operation permissions on all AS resources. |
AutoScaling ReadOnlyAccess | Auto Scaling | Read-only permissions on all AS resources. |
CTS Administrator | Cloud Trace Service | Full permissions for CTS. This policy depends on the Tenant Guest policy in the same project and the Tenant Administrator policy in the OBS project. |
DNS Administrator | Domain Name Service | Full permissions for DNS. This role must be used together with the Tenant Guest and VPC Administrator roles in the same project. |
DNS FullAccess | Domain Name Service | Full permissions for DNS. |
DNS ReadOnlyAccess | Domain Name Service | Read-only permissions for DNS. Users granted these permissions can only view DNS resources. |
ECS Admin | Elastic Cloud Server | All ECS operation permissions, including creating, deleting, and viewing ECSs and modifying ECS specifications. |
ECS User | Elastic Cloud Server | General operation permissions on ECSs (such as viewing and restarting ECSs), but not advanced operation permissions (such as creating or deleting ECSs, or reinstalling/changing ECS OSs). |
ECS Viewer | Elastic Cloud Server | ECS real-only permissions, such as viewing ECSs. |
EVS Admin | Elastic Volume Service | All EVS operation permissions, including creating, deleting, and viewing EVS disks and modifying EVS disk specifications. |
EVS Viewer | Elastic Volume Service | EVS read-only permission, such as viewing EVS disks and EVS disk details. |
IMS Administrator | Image Management Service | Permissions to create, modify, delete, and share images. The permissions depend on the Server Administrator and OBS Tenant Administrator permissions.
|
KMS Administrator | Key Management Service | Users with this set of permissions can perform administrator operations on KMS. |
NAT Gateway Administrator | NAT Gateway | Permissions to create, delete, modify, and query all resources of the NAT Gateway service. The permissions depend on the Tenant Guest permission. If a NAT user needs resources, including VPCs, subnets, and EIPs, to create NAT gateways, the VPC Administrator and Server Administrator permissions are required. |
RDS Administrator | Relational Database Service | Users who have this right, plus Tenant Guest and Server Administrator rights, can perform any operations on RDS, including creating, deleting, rebooting, or scaling up DB instances, configuring database parameters, and restoring DB instances. Users who have this right but not the Tenant Guest or Server Administrator right cannot use RDS.
|
RTS Administrator | Resource Template Service | Permissions to create, modify, and delete resource stacks. |
Security Administrator | Base | Full permissions for IAM. |
Server Administrator | Base |
|
SMN Administrator | Simple Message Notification | Permissions to:
|
Tenant Administrator | Base | Permissions required to perform operations on all cloud resources of an enterprise. |
Tenant Guest | Base | Permissions required to query the usage of all cloud resources of an enterprise. |
TMS Administrator | Tag Management Service | Users with this permission can create, modify, and delete predefined tags. |
TMS Administrator | Tag Management Service | Full permissions for TMS. This role must be used together with the Tenant Guest, Server Administrator, IMS Administrator, AutoScaling Administrator, VPC Administrator, VBS Administrator and Tenant Administrator role in the same project. |
VPC Administrator | Virtual Private Cloud | All permissions on VPC. To be granted the permissions, users must also have the permissions of Tenant Guest and Server Administrator. |
VPC FullAccess | Virtual Private Cloud | All permissions of VPC service. |
VPC ReadOnlyAccess | Virtual Private Cloud | The read-only permissions to all VPC resources, which can be used for statistics and survey. |