Creating a User and Granting DNS Permissions¶
This chapter describes how to use IAM to implement fine-grained permissions control for your DNS resources. With IAM, you can:
Create IAM users for employees based on your enterprise's organizational structure. Each IAM user will have their own security credentials for accessing DNS resources.
Grant only the permissions required for users to perform a specific task.
Entrust another account or cloud service to perform efficient O&M on your DNS resources.
Skip this part if your account does not need individual IAM users.
The following describes the procedure for granting permissions (see Figure 1).
Prerequisites¶
Learn about the permissions.
Process Flow¶
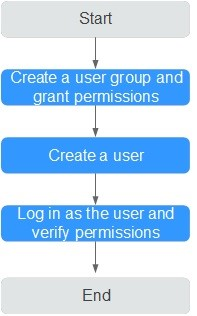
Figure 1 Process for granting permissions¶
Create a user group and grant permissions.
Create a user group on the IAM console and attach the DNS ReadOnlyAccess policy to the group, which grants users read-only permissions to DNS resources.
Create an IAM user.
Create a user on the IAM console and add the user to the group created in step 1.
Log in and verify permissions.
Log in to the DNS console by using the created user, and verify that the user only has read permissions for DNS.
Choose Service List > Domain Name Service. On the DNS console, choose Dashboard > Private Zones. On the displayed page, click Create Private Zone. If the private zone cannot be created, the DNS ReadOnlyAccess policy has already taken effect.
Choose any other service in Service List. If a message appears indicating that you have insufficient permissions to access the service, the DNS ReadOnlyAccess policy has already taken effect.